Effortless security testing for embedded software.
Expose hidden bugs using scalable automated fuzz testing without hardware. Ship embedded software faster, safer, and always compliant.

Fuzz what you ship.
Fuzzware brings clarity to the black box of embedded software.
We remove the hardware barrier from embedded software testing.
So teams can test deeper, ship faster, and trust their software.
Built on intelligent foundations
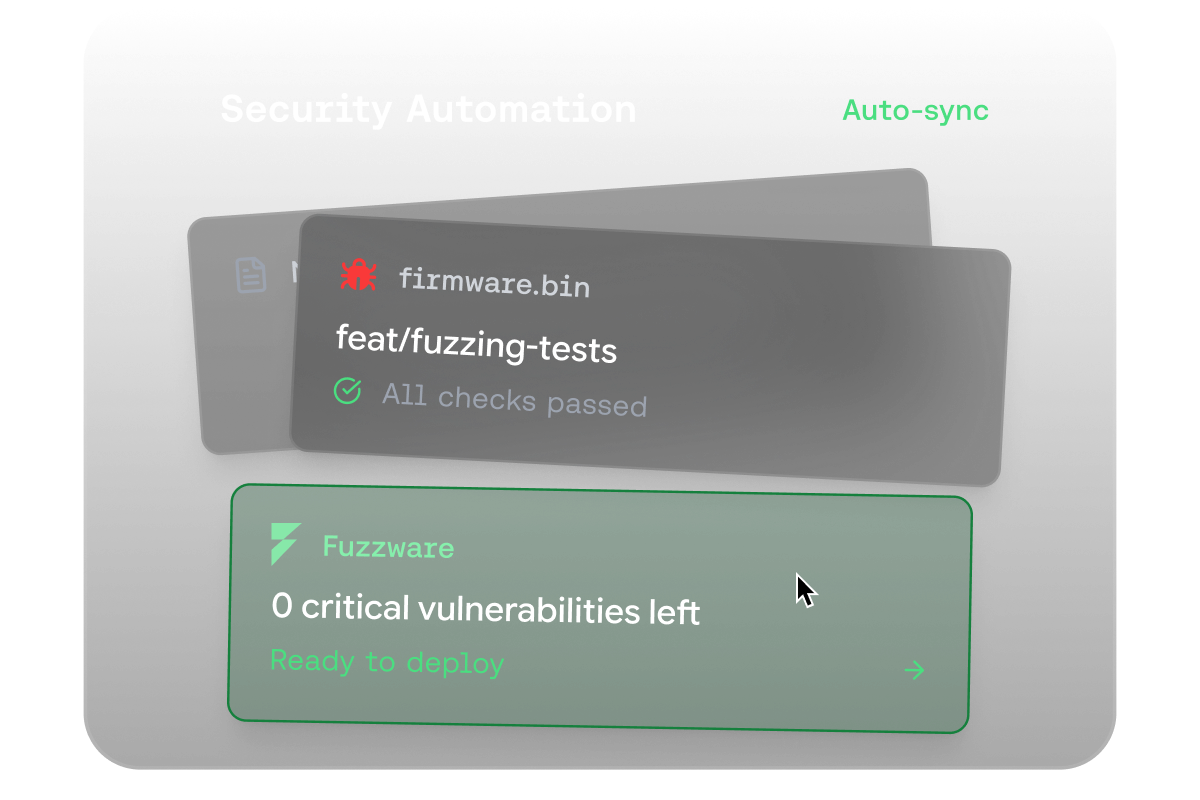
Fuzzware combines advanced emulation, automated fuzzing, and intelligent analysis to uncover vulnerabilities hidden deep inside firmware. Under the hood, powerful systems work together to make testing faster, safer, and more insightful.
No Hardware Needed
Fuzzware enables efficient security testing without physical hardware. Through advanced firmware rehosting, it delivers a scalable and cost-effective analysis, simplifying processes and eliminating logistical overhead.
Binary Only
Fuzzware tests binaries directly, allowing closed-source and third-party firmware to be analyzed without exposing source code. It strengthens supply-chain security while keeping intellectual property protected.
Full System Fuzzing
Unlike conventional tools, Fuzzware fuzzes the complete system as it runs in production. This ensures realistic results and full coverage, not just isolated component testing.
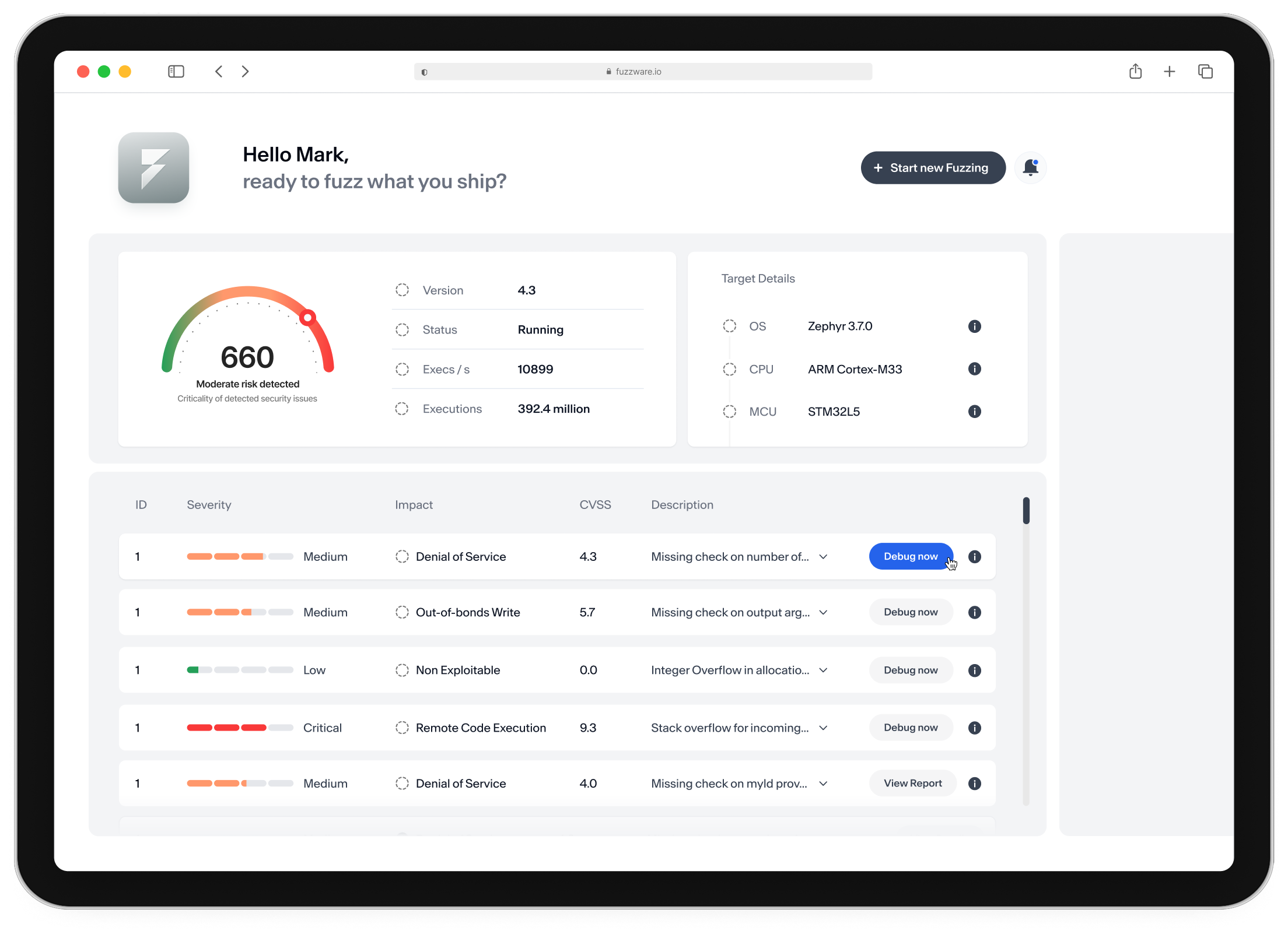

Fuzz smarter to
ship faster.
Fuzzware automates the whole process of testing firmware, from emulation to discovering security vulnerabilities. Each feature is designed to simplify complex workflows and deliver actionable security insights faster.
Simple. Automated. Hardware-free.
Fuzzware transforms firmware security testing into a streamlined, hardware-free workflow — combining expert validation, automated fuzzing, and compliance-ready reporting in a clear, repeatable process.


From firmware analysis
to compliance-ready results
Fuzzware supports security teams from deep firmware analysis to compliance-ready results by combining automated fuzzing, expert research, and structured documentation.
End-to-end
fuzzing audit
Our experts perform a full end-to-end audit of your embedded software. We require only your compiled software to start the audit.
Compliance
guidance
Are the fuzzing results required for compliance? We can help you document the test in a compliance-ready manner.
Vulnerability
Verification
Found vulnerabilities are classified and verified by our experts. We provide a detailed report and meaningful solution recommendations.
From Academic Excellence to Industry Innovation
Fuzzware was founded by Simon Wörner and Tobias Scharnowski, two PhD researchers from CISPA Helmholtz Center whose award-winning firmware fuzzing research is now transforming embedded systems security for companies worldwide.

Tobias is Research Lead at Fuzzware and a doctoral student at CISPA Helmholtz Center for Information Security. His research focuses on automated firmware security analysis for embedded systems. As a CTF veteran and repeat Pwn2Own participant, he has demonstrated practical exploits in automotive and industrial automation domains, including critical vulnerabilities in the DNP3 implementation that powers the US electric grid.

Simon is a PhD researcher at CISPA Helmholtz Center for Information Security, specializing in embedded systems security and firmware fuzzing. His research focuses on innovative fuzzing techniques for firmware analysis. With multiple publications at leading conferences, including USENIX Security, he brings deep technical expertise to Fuzzware's product development.
Have Questions About Firmware Fuzzing?
Connect with Simon and Tobias to explore how Fuzzware fits your security workflow.
Frequently Asked Questions
Get answers to common questions about Fuzzware's hardware-free fuzzing approach, technical capabilities, and how we help teams secure their embedded systems faster and more effectively.
Fuzzware performs comprehensive full-system fuzzing that tests your firmware exactly as it runs in production. Unlike isolated unit tests, we analyze the complete interaction between software components, peripheral interfaces (MMIO), and interrupt handlers. Our automated analysis identifies vulnerabilities such as memory corruptions, buffer overflows, and use-after-free bugs in both first-party and third-party firmware binaries. We focus on discovering security-critical issues that could lead to exploitation, privilege escalation, or denial of service in your embedded devices.
Static analysis examines code without executing it, which can miss runtime vulnerabilities and produce false positives. Penetration testing requires physical hardware and extensive manual effort. Fuzzware solves these shortcomings through a full-system dynamic analysis: we automatically execute your firmware in a virtual environment, testing real execution paths under realistic conditions. This approach achieves significantly higher code coverage than static tools while being infinitely more scalable than manual penetration testing. Our technique discovers vulnerabilities that traditional methods miss, especially in complex firmware interactions.
Fuzzware currently supports a wide range of ARM Cortex-M architectures (M0, M3, M4, M7), which are used in the majority of embedded systems across industries, including medical devices, IoT, automotive, and industrial control systems. Our emulation framework accurately models Memory-Mapped I/O (MMIO) interactions, allowing us to test firmware without requiring physical hardware specifications. We continuously expand our architecture support based on customer needs. If you're working with a specific architecture, contact us to discuss compatibility and potential support.
Fuzzware is specifically designed to work with binary-only firmware, requiring no source code or documentation. This makes us uniquely suited for analyzing closed-source components, third-party libraries, and legacy firmware where source code is unavailable. Our advanced emulation and analysis techniques automatically model hardware interactions and identify security vulnerabilities purely from the compiled binary. This capability is essential for a comprehensive security assessment of modern embedded systems that integrate multiple proprietary components from different vendors.